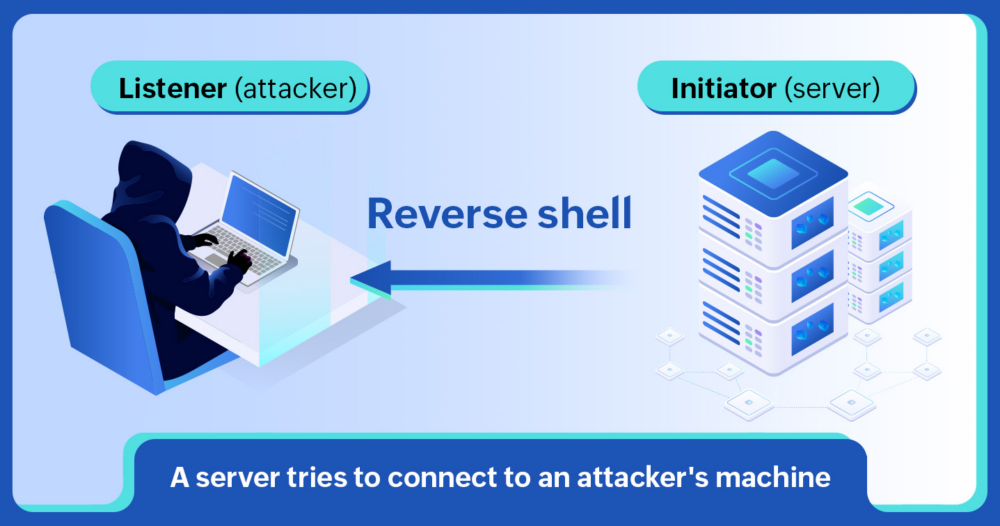
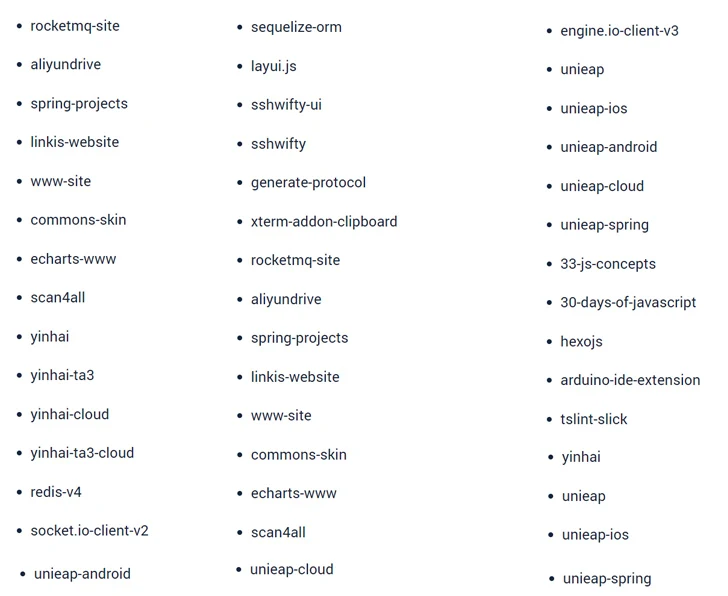
A new set of 48 malicious npm packages has been discovered in the npm repository, capable of deploying a reverse shell on compromised systems. These packages, cleverly disguised to seem legitimate, contain obfuscated JavaScript that triggers a reverse shell upon installation. They were published by an npm user named hktalent, with 39 of them still available for download.
The attack occurs after package installation through an install hook in the package.json file, executing JavaScript code to establish a reverse shell connection to rsh.51pwn[.]com. The attacker deployed benign-sounding packages with multiple layers of obfuscation and deceptive tactics to target any machine installing them.
These findings follow recent revelations of malicious code in two Python packages, localization-utils and locute, which aimed to steal sensitive data from Telegram Desktop. These packages retrieved a final payload from a dynamically generated Pastebin URL and sent the data to an actor-controlled Telegram channel.
This development underscores the growing interest of threat actors in open-source environments, enabling impactful supply chain attacks affecting multiple downstream customers simultaneously. Such packages demonstrate dedicated efforts to evade detection, emphasizing the critical importance of trust in dependencies within our open-source ecosystems, as noted by Phylum, a software supply chain security firm.